The blockchain: blocks, token and Addresses
In the following, the concept of a blockchain is introduced schematically using a simplified architecture. The mechanisms presented here in simplified form are fundamental to the functionality of real existing blockchains, but are only described here to the extent that is necessary for a basic understanding.
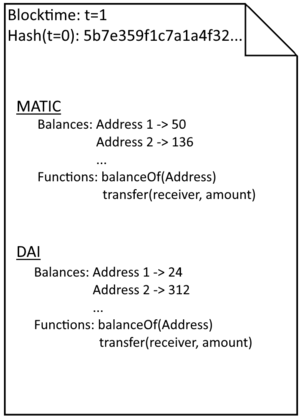
A single block can be understood as a simple piece of paper with a well-defined and structured content: The Header is given by the so called blocktime that is comparable to the page numbering within a book. Additional, the hash of the previous block finds place in some form within the header. On the rest of the page, the various data for each token are noted. This is shown as an example for MATIC and DAI.
Each token has its own storage to keep track of who holds how much of them: a list of balances. In addition, there are executable functions that can differ from token to token, with certain standard functions being common to most tokens: one function is usually goven to determine the balance of a given address (similar to an account number) and another function enables payments, i.e. token transfers. Likewise, each token is given a name and a symbol, an abbreviation usually three to five characters long. Arbitrary other functionalities can be implemented and interact with other tokens via their respective functions. This interoperability enables the programming of decentralized marketplaces, democratic voting and much more. A single block is basically a listing of the account balances of all tokens, as well as all relevant properties of the tokens - one speaks of states: a block is the listing of all current states of all tokens of the respective blockchain.
The addresses are alphanumeric codes associated with a user ("account holder"), for example 0x1BE2a117E255e147c56021224d11e13E79121Be1. The functionality of a token is usually defined in relation to the address of the respective user: for example, each user can only transfer tokens that are assigned to an address that he or she controls. Also each token has an address associated with it: addresses are associated with storage locations within the block. Using tokens one usually refers to them via their name or symbol but one is adviced to keep also track of the tokens address to prevent (potential lossy) mistakes.
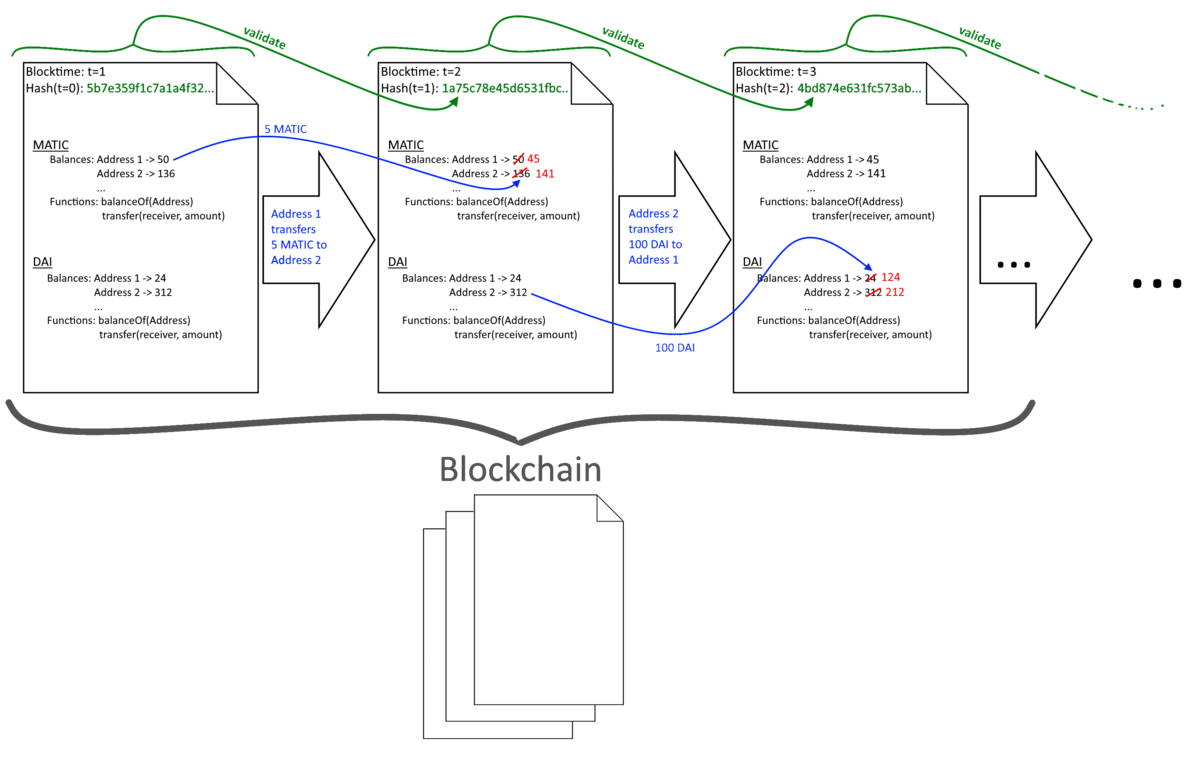
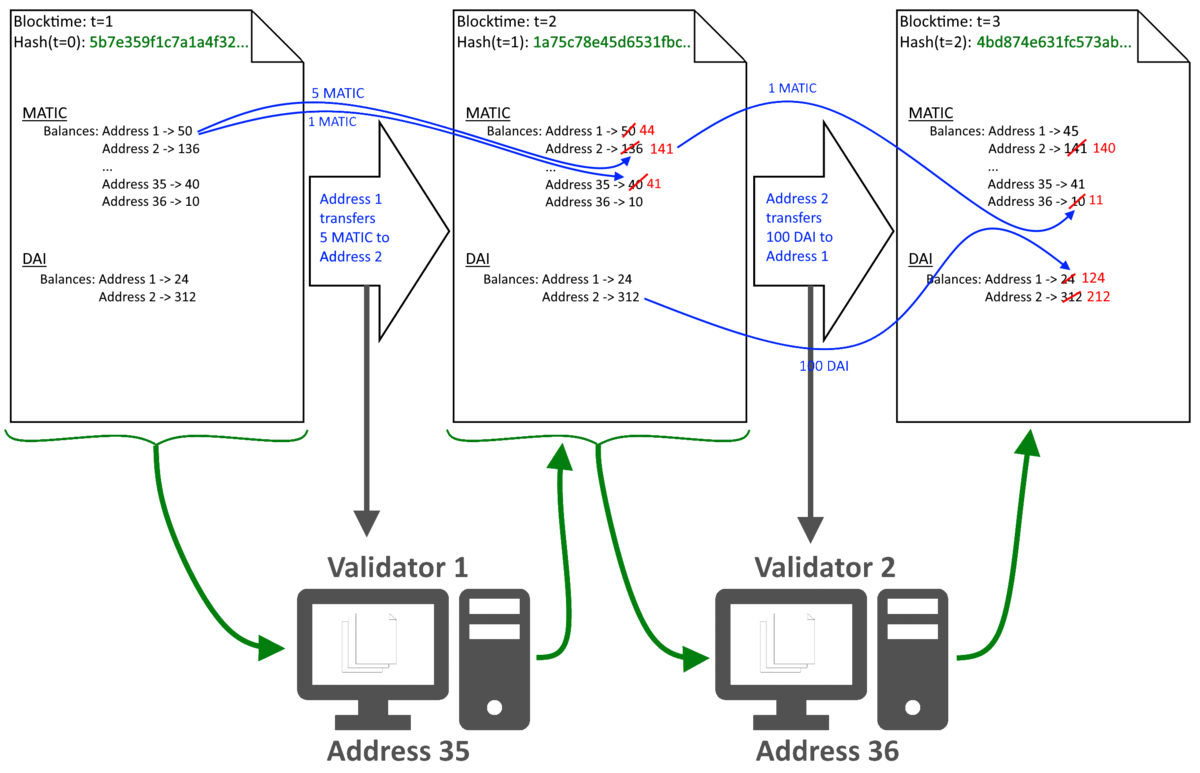
Each interaction with the blockchain that cause a state transition is referred to as a transaction - for example the transfer of a token: With a user transferring five token from his address "Address 1" to a different address "Address 2", the following modifications are executed: The Balance of "Address 1" is reduced by five and the balance of "Address 2" is increased by five. (Of course, we require that the Balance of "Address 1" was at least 5 before the state transition.) For each transaction it is checked if it was caused by an address that is authorized to perform this state transition. After the state-transition, the state state is changed and a new block with modified balances - a new piece of paper finds its way onto the present staple. This staple is referred to as Blockchain:
The creation of a new block is called validating or mining. During this procedure, the validity of the new block is verified: For example, it is checked if the Hash in the blocks header is valid and corresponds to the previous block. If this is not the case, the new block is rejected and the blockchain reverts to the last valid state. This guarantees that each block has a valid predecessor. It is also checked whether or not the transaction was caused by an address that is authorized to execute the relevant function. If this is not the case, the block gets rejected. Who is authorized is determined with reference to cryptographic methods and we will take a look at the two main gradients of the procedure: elliptic curve cryptography and hashes:
- Each address that is controlled by a user corresponds to two cryptographic keys: a public key and a private key. If any text or data gets encrypted with of these wo keys it can be decrypted with the other key. This elliptic encryption is also used for secured communication (for example the SSL protocoll for Https): The message to be send is encrypted with the public key of the receiver and the encrypted message is sent. Only the receiver with his private key can decrypt the message again.
- Another important ingradient is hashing: A hash can be compared to a fingerprint of given data. During hashing arbitrary long input gets reduced to an alphanumeric code sequence of fixed finite length. Ethereum like blockchains use the Keccak-256 hashing algorithm. The hash of the text "Hello World." is given by "6ac466601079053c254ab4f5750b05b5e881997738ed1d6dd3db2f8917ab8563". The minor modification of the input text to"Hello World!" results in a completely different hash "3ea2f1d0abf3fc66cf29eebb70cbd4e7fe762ef8a09bcc06c8edf641230afec0."
How these two ingredients can be used during validating a block is presented in the following:
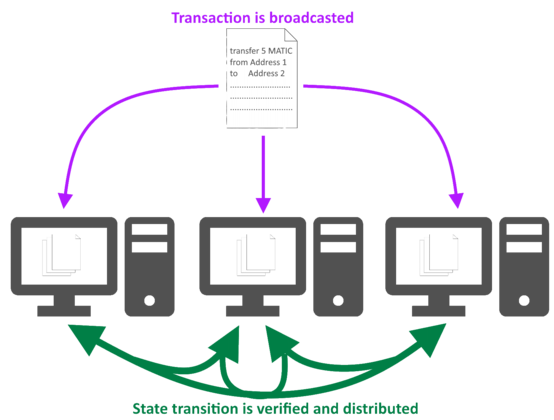
A transaction is encoded by a given address. The corresponding state transition is now hashed and this hash encrypted with the private key that belongs to the address. The state transition and its encoded hash (referred to as a signature) is now broadcasted to validators or miners. They decode the transmitted hash using the public key of the sender and they hash the state transition: Only if the two are identical can the transaction be valid. In addition it is checked if the address is allowed to execute the relevant functions for the state transition. Only if this is the case, the new block is accepted. Each accepted block is then distributed within the network of validators and miners so that each of them has the present state of the blockchain.
Due to the transparency of this procedure, its validity can eb checked by anyone: Each trial of manipulation of the blocks can be detected with corresponding software and gets obvious the moment an uncorrupted validator looks at the block and reverts the state to the last valid one. The security of the systems requires that the same validator does not validate too many consecutive blocks. Hence, it is in the interest of the blockchain to have sufficiently many independent validators.
Due to the complexity of the cryptographic algorithms this procedure is computational intensive and requires quite some effort of the validators or miners. To compensate them for their effort, each Blockchain has a native Token or Coin: On Ethereum this is Ether, on PolkaDot it is Dot and on Polygon it is MATIC. For each transaction a fee has to be paid to the validator by giving some of the chains native currency:
The Wallet
With conventional cash, the wallet contains the means of payment in the form of coins and bills. This is not the case with blockchains: there is no token in the wallet, only the key pair of private and public keys is stored in it, usually in encrypted form, and is used to sign transactions. Wallets come in a variety of forms: Paper wallets are actually just a piece of paper on which both keys are written. As a so-called cold wallet, they allow the secure storage of tokens, but not their use: This requires a hot wallet, i.e. one that can be used directly to sign transactions. Such wallets can be available as a hardware wallet, such as the Ledger Wallet, as a browser addon, such as Metamask, or as a mobile app, such as MEW. Just as web browsers represent a door to the "normal" Internet, Web2, wallets allow access to the Web3 by enabling the use of decentralized Apps (DApps). There are wallets compatible with multiple blockchains, as well as blockchain-specific wallets.
Instead of the private key, a mnemonic passpgrase is often used: a fixed number of consecutive words that encode the private key. Neither this mnemonic nor the private key should ever fall into the wrong hands - they allow complete control of the wallet.
Smart Contracts
The functionality of a blockchain and its tokens is based on small programms stored on the blockchain. These are called Smart Contracts on Ethereum-alike Blockchains (EVM-compatible). They implement specific interfaces, functions that can be executed by a user with his address. As exmaples we already mentioned the functions balanceOf(address) and transfer(receiver, amount). To each Token there is a corresponding Smart Contract implementing its functionalities. On EVM-compatible Blockchains Smart Contracts are coded using the language Solidity, other Blockchains use Rust or variants of C++ or Javascript.
Smart contracts can be almost arbitrarily complex implementing functionalities that go far beyond simple tokens, but they have one limitation: Blockchains are closed systems. The interaction of different Smart Contracts requires them to be placed on the same Blocchain. Hence, it is for example not possible to use Bitcoin on Ethereum or Ethereum on Bitcoin. In order to circumvent this obstacle, a certain mechanism is set up using so-called bridge contracts.
Different species of token
The following classification of different token types is not necessarily universal and is more technically motivated. There are other classifications that use a legal basis instead of a technical one. Only an initial, rough overview of the various systems is to be given here. The delimitations are often not clear, since mixed forms of token exist. Because it is becoming increasingly difficult to distinguish between tokens and coins, we consider these terms to be synonymous.
The Blockchains native currency
The Blockchains native currency results from the Blockchains functionality, which requires Validators to be paid. It enables the usage of the Blockchain by allowing to submit Transactions. There is no central authority in control of its monetary policies, it is organized as a decentralized democratic system.Exmaples are: Bitcoin (BTC), Ethereum (ETH), Polygon Matic (MATIC), Avalanche (AVAX), PolkaDot (DOT), Cosmos Atom (ATOM), Solana (SOL), Ada Cardano (ADA), VeChain (VET), Dash (DASH).
Liquidity Token
On blockchainst there are various financial tools that hardly have a direct counterpart in the classic economy, but rather correspond to mixed forms of joint ventures, shares and any type of company. They are often related to the concept of liquidity provision: an investor puts one or more tokens into a decentralized system to allow for its functionality. In return he receives tokens that represent the value that he has put into the system. Two examples are presented below:
Decentralized Exchanges (DEXs) eallow to swap between different Token. They can be compared to a money exchange without single owner or central controlling authority:
Everyone can participate in the DEX by providing those tokens tradable on the market and in return receiving liquidity-tokens that represent the corresponding share on the total market. Exchange fees levied in the DEX are credited proportionately to the liquidity token owners. The value that is inserted into the DEX is exposed to the price fluctuations of the tradeable tokens in non-trivial way. As soon as you redeem a liquidity token, the shares in the various tokens in the marketplace including the share in the exchange fees charged are paid out. Examples of this are the tokens you get when you open a liquidity pool or participate in an existing one: This is, for example, possible at UniSwap, Curve or Balancer.
Another form of liquidity pool enables the granting of loans. Here, the appropriate tokens are made available to the pool, allowing them to be awarded as credit. The tokens earned for bringing capital into the pool correspond to asset shares and the interest earned from lending is prorated by these asset shares. As exmaple one can look at the Aave protocol.
Liquidity token make it possible to share in the profits of operational business from decentralized companies at the cost of bearing a part of the risk.
Governance Token
With many decentralized systems, there are parameters that can be adjusted or decisions regarding the operative business have to be made. Control over such systems is not left to a central, corruptible authority, but is democratically divided among the system participants. For this purpose, a token is introduced, which acts as a voting weight for corresponding votes.
Stablecoins
Stablecoins are special tokens that aim to reproduce or replicate the price of another asset or resource, making them usable on the blockchain. There are two different forms of it: With direct-collateralized stablecoins, the asset whose price is to be replicated is deposited directly as collateral. There is usually a company that operates the corresponding token and ensures that the appropriate security is deposited for each token that is issued. The company acts as the central authority here and is responsible for the custody and release of deposited collateral. In the case of indirectly secured stablecoins, a different asset than the one whose price shall be mimicried is put in as collateral and the price replication is based on algorithmic interaction with various decentralized marketplaces. Indirectly secured stablecoins can work without a central authority if they only accept forms of asset existing on the blockchain (i.e. tokens) as collateral
Equity- oder Security-Token
This type of token is similar to traditional stocks or other traditional financial tools that represent a stake in a company, project or product. They are often associated with profit sharing, ownership shares and voting rights and thus have an overlap with almost all of the aforementioned token types. Compared to liquidity tokens, we assume here that the operative business of the respective company takes place primarily outside the blockchain. This type of token thus represents an interface between "onchain" and "offchain" economy.
A special type of equity or security token is given by so-called wrapped coins: Here, a token of one blockchain is replicated by a token on another blockchain. An example of this is the Wrapped Bitcoin (WBTC) on Ethereum and Polygon, which replicates the Bitcoin (BTC).
Dezentrale Autonome Organisationen (DAOs)
DAOs are the blockchain equivalent of legal entities: A group of people - often only loosely connected - who are pursuing a common goal. This can be the operation of a decentralized system, the management of a stable coin or the creation of a product. To structure itself, the DAO uses a wide variety of tokens: One or more DAO-external tokens often serve as a means of payment for the various DAO-internal tokens. How the value raised by selling different internal tokens is usually decided democratically using a governance token. This Gorvernance token can be purchased or earned through active participation in the DAO. The operative business of the DAO is often represented by various equity or security tokens and thus made accessible to the market. Besides most blockchains in general, examples of DAOs are
- The Token Engineering Commons, striving for Sustainable & Ethical Design for Token Ecosystems
- The MakerDAO, managing DAI
About the Author
Dipl.-Ing. Dr.rer.nat. Rudolf Golubich, BSc has a background in physics and is the founder of the Hvergelmir Cooperation and offers also service in data science, statistics and data engineering. Within the cooperation, he serves as a generalist and Token Engineer and is responsible for the analysis and development of protocols that go beyond the standard.